ConfigMgr Compliance of Windows Defender
ConfigMgr has some great features and I recon one that is sorely underutilized and appreciated is Compliance.
It can prove challenging managing an Enterprises, ensuring critical settings have not been skewed or altered over time. The problem is that we just can't be 100% sure that the system is as intended, but with ConfigMgr's Compliance those critical services or settings can be monitored and even remediated.
The following example validates that Windows Defender and its Definition Updates are working and up to date. I've used similar with Symantec and expect other AV providers to work similarly. For this demo I've used a simple bit of PowerShell, but it's pretty extensible and can be used to validate anything you can code.
Script Discovery can use PowerShell, VBScript and JScript. There are other options available such as AD Query, Assembly, File, Registry, SQL, WQL and Xpath queries.
For this tutorial 3 validations will be configured, definitions are no older than 1 day, Defender service is running and finally that Real Time Protection is enabled.
Open the ConfigMgr Console and browse to 'Administration' and 'Client Settings'.

Select 'Yes' for the 'Enable compliance evaluation on clients'

Now right click on the settings and deploy to the Workstations Collection, if it hasn't already been done.
Browse to 'Assets and Compliance' and open up 'Compliance Settings'

'Configuration Items' are the individual settings being tested, these are assigned to 'Configuration Baselines' and the baseline is deployed to a Collection.
The 'Configuration Item' will ensure that Definition Updates are up to date and if not update them.
Right click 'Configuration Items' and 'Create Configuration Item'

Name and select 'Windows Desktops and Servers (Custom)'

Select the version of the Windows client

Select the version of the Windows client, click 'Next'
And on the Settings window, click 'New'
On the General tab, add the 'Name', select Script for 'Setting Type' and String for 'Data Type'
Click on and add both a Discovery Script and Remediation Script (Optional) and add the follow corresponding scripts

Discovery Script
The script will check the creation date of mpengine.dll and that its no older than one day.

$defUpdates = Get-ChildItem "C:\ProgramData\Microsoft\Windows Defender\Definition Updates\" -Filter "*{*"
$mpEngine = Get-ChildItem $defUpdates.FullName -Filter "mpengine.dll"
if (((get-date) - $mpEngine.creationTime).days -lt 1){Write-Output "true"}
else {Write-Output "false"}
Remediation Script
If mpengine.dll fails the discovery script and is older than 1 day a forced Windows Definition update is run

& "C:\Program Files\Windows Defender\MpCmdRun.exe" -SignatureUpdate
Now click on 'Compliance Rules' and 'New'

Complete the Compliance Rule

Complete the wizard and finish this item.
Now for the second item, this will check that Real Time Protection is enabled in policy.
Repeat the wizard but select 'Registry Value'
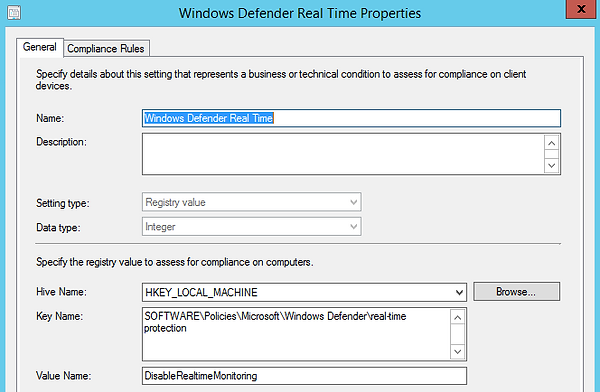
Compliance Rule will test for the value of 0
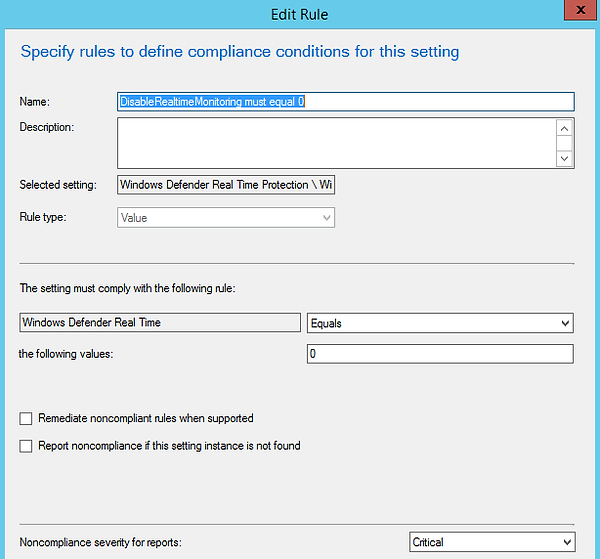
Lastly, validate that the Windows Defender Service is running and remediate it to start if its stopped.
Again follow the previous instructions and insert the extracts from below.

$svc = Get-Service -Name WinDefend
if ($svc.Status -ne "Running"){Write-Output "False"}
else {Write-Output "True"}

Start-Service -name WinDefend

Thats the 3 Configuration Items created, now to create and assign to a Configuration Baseline

Right click on 'Configuration Baselines' and 'Create Configuration Baseline'

Name, then click 'Add' and select 'Configuration Items'

Select each Windows Defender item and click 'Add'

Check 'Evaluate this baseline to improve searching and filtering'

Now right click on the Windows Defender Baseline and 'Deploy'

Check the 'Remediate noncompliant rules when supported' and 'Allow remediation outside the maintenance window'
Click 'Browse' and select either a test collection or a collection that contains Workstations
Change the schedule to 6 hours, as you'll be wanting to run during the working day whilst the workstations are powered on.

From a client open 'Control Panel' and then 'Configuration Manager' and click on 'Machine Policy Retrieval .......' to pull down the Baseline, this may take a few minutes.

After a few minutes the Baseline will be available in the 'Configuration' tab, click 'Evaluate' and then 'View Report'

To view the report will require elevated rights, but as you can see everything is compliant.

To check for compliance across the enterprise run 'Summary compliance by configuration baseline' ConfigMgr report.

To prove that compliance is in fact working, I'm going to disable Real Time Protection in GPO.
To change the GPO 'Group Policy Creator Owners', DA or Delegated Edit permissions over the GPO will be required.
Enable the current Disabled 'Turn off real-time protection' in GPO

Run Regedt32 and browse to 'HKLM:\Software\Policies\Microsoft\Windows Defender\real-time Protection'
Run 'gpupdate /force' and the 'DisableRealTimeMonitoring' value will change from 0 to 1

Back to Configuration Manager applet in the Control Panel and Configurations.
Click on 'Evaluate' and then 'View Report'
The summary will report non-compliant for 'Windows Defender Real Time Protection'

Drill a bit further into the non-compliant status, it will clearly show the expected value of 0 is now a 1

