Health and Vulnerability Script for Windows, Servers and DC's
The vulnerability script is now only available upon request. Send requests via the contact form on the homepage.
The SecureReport script is designed to detect vulnerabilities and common misconfigurations within Windows and installed applications. While scanners like Nessus operate network-wide, this script provides a comprehensive audit of security concerns, executed locally for a deeper analysis.
Hackers or disgruntled employees could exploit these vulnerabilities, potentially leading to privilege escalation from user to system access and ultimately gaining Domain Admin privileges.
The vulnerability script underwent testing on the most recent iterations of Windows 11, and Server 2022, requiring PowerShell version 5.1 to generate an HTML output. Notably, PowerShell version 4 lacks support for '-depth', hindering the audit of File, Folder, and Registry permissions. Windows 8, 8.1, 2012, and 2012 R2 necessitate an update to Windows Management Framework 5.1 for compatibility.
Do not make changes to your IT systems based on the output of this report without a backup or testing, some of the suggestions are aimed at Domain joined clients and are likely to prevent Linux or legacy services from connecting to the domain.
#Downloading and Executing the Script
Download Tenaka/SecureReport (github.com), and launch from either PowerShell or PowerShell_ISE with Administrative privileges. The report will take a while to execute, potentially up to 30 minutes, please be patient.
The report output is saved to C:\Securereport\FinishedReport.htm
The html output can be imported into Excel for further analysis and uses the True and False values as a drop-down filter.
Open Excel, Data, Import from Web. Enter the file path in the following format file:///C:/SecureReport/NameOfReport.htm, then select multiple items and click on Load and select 'Load To', click on Table.
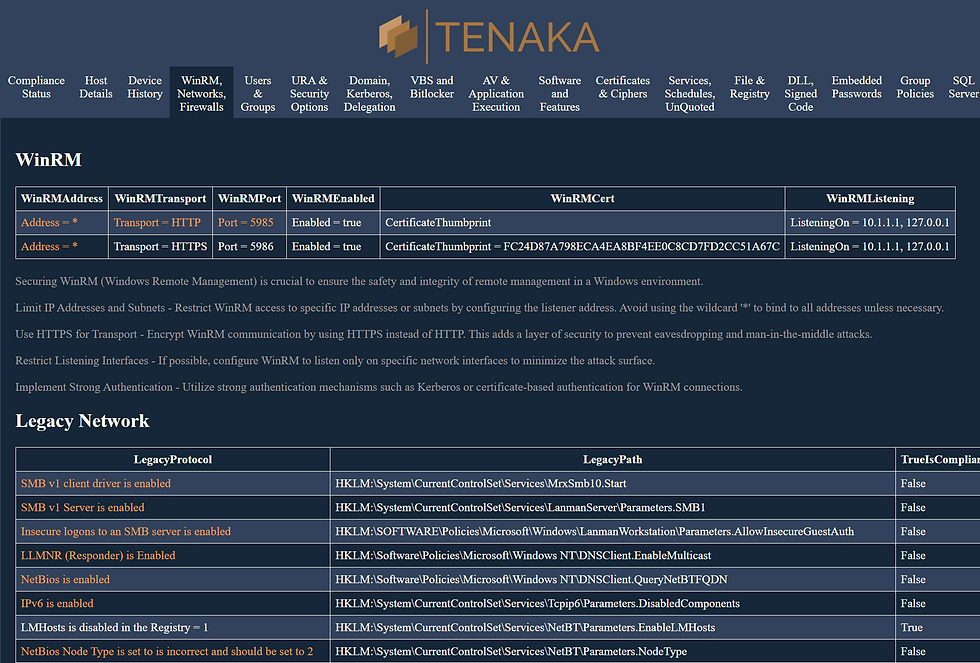



#List of checks and balances:
Host Details, CPU, Bios, Windows Version
Accounts, Groups and Password Policy
User Rights Assignments
Install Applications and installed Windows Updates
Virtualization, UEFI, Secure Boot, DMA, TPM and Bitlocker Settings
LSA, DLL Safe Search Order, Hypervisor Code Integrity
DLL Hijacking
Files not Signed (Authenticode)
Autologon Credentials in the Registry
Unquoted paths
Processes that contain passwords in the command line
Enabled legacy Network protocols
Registry Keys with weak Permissions
System Folders with weak Permissions
Drivers not Signed
Authenticode Hash Mismatch
Windows, Edge and Office 2016-365 GPO comparison against Microsoft recommend.
Firewall settings and rules
Active Directory Account and SPN issues
SQL Server
#URA
User Rights Assignments (URA) control what tasks a user can perform on the local client, server or Domain Controller.
For example, the ‘Log on as a service’ (SeServiceLogonRight) provides the rights for a service account to Logon as a Service, not Interactively.
Access to URA can be abused and attack the system.
Both SeImpersonatePrivilege and SeAssignPrimaryTokenPrivilege are commonly used by service accounts and vulnerable to an escalation of privilege via Juicy Potato exploits.
Access this computer from the network (SeNetworkLogonRight) allows pass-the-hash when Local Admins share the same password, remove all the default groups and apply named groups, separating client from servers."
Further details can be found @ https://docs.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/user-rights-assignment
#TPM and Bitlocker
"TPM and Bitlocker protect against offline attack from USB and mounting the local Windows system then accessing the local data. 'TPM and Pin' enhances Bitlocker by preventing LPC Bus (Low Pin Count) bypasses of Bitlocker with TPM.
Further information can be found @
https://www.tenaka.net/bitlocker
#Secure Boot
Secure Boot is a security standard to ensure only trusted OEM software is allowed at boot. At startup the UEFi and boot software's digital signatures are validated preventing rootkits
More on Secure Boot can be found @
#VBS
Virtualization-based security (VBS), isolates core system resources to create secure regions of memory. Enabling VBS allows for Hypervisor-Enforced Code Integrity (HVCI), Device Guard and Credential Guard.
Further information can be found @
https://docs.microsoft.com/en-us/windows-hardware/design/device-experiences/oem-vbs
https://www.tenaka.net/deviceguard-vs-rce
https://www.tenaka.net/pass-the-hash
#Hypervisor Enforced Code Integrity
Hypervisor Enforced Code Integrity prevents the loading of unsigned kernel-mode drivers and system binaries from being loaded into system memory.
Further information can be found @
#Security Options
Prevent credential relay with Impacket and Man in the Middle by Digitally Signing for SMB and LDAP connections enforcement.
Further information can be found @
https://www.tenaka.net/smb-relay-attack
#LSA
Enabling RunAsPPL for LSA Protection allows only digitally signed binaries to load as a protected process preventing credential theft and access by code injection and memory access by processes that aren’t signed.
Further information can be found @ https://docs.microsoft.com/en-us/windows-server/security/credentials-protection-and-management/configuring-additional-lsa-protection
#DLL Safe Search
When applications do not fully qualify the DLL path and instead allow searching the default behaviour if for the ‘Current Working Directory’ called 2nd in the list of directories. This allows an easy route to call malicious DLLs. Setting ‘DLL Safe Search’ mitigates the risk by moving CWD to later in the search order.
Further information can be found @
https://docs.microsoft.com/en-us/windows/win32/dlls/dynamic-link-library-search-order
#DLL Hijacking (Permissions)
DLL Hijacking is when a malicious DLL replaces a legitimate DLL due to a path vulnerability. A program or service makes a call on that DLL gaining the privileges of that program or service. Additionally, missing DLLs presents a risk where a malicious DLL is dropped into a path where no current DLL exists but the program or service is making a call to that non-existent DLL.
This audit is reliant on programs being launched so that DLLs are loaded. Each process’s loaded DLLs are checked for permissions issues and whether they are signed.
The DLL hijacking audit does not currently check for missing DLLs being called. Process Monitor filtered for ‘NAME NOT FOUND’ and path ends with ‘DLL’ will.
#Automatically Elevate User
Auto Elevate User is a setting that elevates users allowing them to install software without being an administrator.
#Password in Files
Searches the following locations:
C:\Users\
C:\ProgramData\
C:\Windows\System32\Tasks\
C:\Windows\Panther\
C:\Windows\system32\
C:\Windows\system32\sysprep
Searches the following file extensions:
txt, ini, .xml
For the following words:
password, credential
Ignore these files as they contain the word 'Password' by default:
C:\Windows\system32\NarratorControlTemplates.xml
C:\Windows\system32\DDFs\NGCProDDF_v1.2_final.xml
C:\Windows\system32\icsxml\ipcfg.xml
C:\Windows\system32\icsxml\pppcfg.xml
C:\Windows\system32\slmgr\0409\slmgr.ini
C:\Windows\system32\winrm\0409\winrm.ini
#Password embedded in Processes
Processes that contain credentials to authenticate and access applications. Launching Task Manager, Details and add ‘Command line’ to the view.
#AutoLogon
Checks "HKLM:\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon" for any clear text credentials remaining from a MECM\SCCM\MDT deployment.
#Unquoted
The Unquoted path vulnerability is when a Windows Service's 'Path to Executable' contains spaces and is not wrapped in double-quotes providing a route to System.
Further information can be found @
https://www.tenaka.net/unquotedpaths
#Legacy Network Protocols
LLMNR and other legacy network protocols can be used to steal password hashes.
Further information can be found @
https://www.tenaka.net/responder
#Permissions Weakness in Default System Directories - Write
System default Folders that allow a User the Write permissions. These can be abused by creating content in some of the allowable default locations. Prevent by applying Execution controls eg Applocker.
Searches:
C:\PerfLogs
C:\Program Files
C:\Program Files (x86)
C:\Windows
Expected folders that a user can Write to:
C:\Windows\System32\LogFiles\WMI
C:\Windows\System32\Microsoft\Crypto\RSA\MachineKeys
C:\Windows\System32\Tasks
C:\Windows\System32\Tasks\Microsoft\Windows\RemoteApp and Desktop Connections Update
C:\Windows\SysWOW64\Tasks
C:\Windows\SysWOW64\Tasks\Microsoft\Windows\RemoteApp and Desktop Connections Update
C:\Windows\tracing
Further information can be found @
https://www.tenaka.net/unquotedpaths
https://www.tenaka.net/applockergpo
#Permissions Weaknesses in Default System Directories - Create Files
System default Folders that allow a User the CreateFile permissions. These can be abused by creating content in some of the allowable default locations. Prevent by applying Execution controls eg Applocker.
Expected folders that a user can CreateFiles to:
C:\Windows\PLA\ReportsC:\Windows\PLA\Reports\en-GB
C:\Windows\PLA\Reports\en-US
C:\Windows\PLA\RulesC:\Windows\PLA\Rules\en-GB
C:\Windows\PLA\Rules\en-US
C:\Windows\PLA\Templates
C:\Windows\Registration\CRMLog
C:\Windows\System32\Com\dmp
C:\Windows\System32\spool\drivers\color
C:\Windows\System32\spool\PRINTERS
C:\Windows\System32\spool\SERVERS
C:\Windows\SysWOW64\Com\dmp
C:\Windows\SysWOW64\Tasks\Microsoft\Windows\PLA
C:\Windows\SysWOW64\Tasks\Microsoft\Windows\PLA\System
C:\Windows\TasksC:\Windows\Temp
C:\Windows\Temp\MsEdgeCrashpad
C:\Windows\Temp\MsEdgeCrashpad\reports
Further information can be found @
https://www.tenaka.net/unquotedpaths
https://www.tenaka.net/applockergpo
#Permissions Weaknesses in Non-Default Directories
A vulnerability exists when enterprise software has been installed on the root of C:\. The default permissions allow a user to replace approved software binaries with malicious binaries.
Further information can be found @
https://www.tenaka.net/unquotedpaths
#Files that are Writeable
System files that allow users to write can be swapped out for malicious software binaries.
Further information can be found @
https://www.tenaka.net/unquotedpaths
#Firewalls
Firewalls should always block inbound and exceptions should be to a named IP and Port.
Further information can be found @
https://www.tenaka.net/whyhbfirewallsneeded
