Zero Trust for the Home Lab - Yubikey and Domain Smartcard Authentication Setup (Part 6)
- Tenaka

- Jun 7, 2025
- 6 min read
Updated: Nov 10, 2025
The Road to the World's Most Secure Home Lab....
So far in the pursuit of the World's most secure home lab, the following have been implemented:
Related Posts:
Part 1 - Zero Trust Introduction
Part 3 - pfSense and 802.1x
Part 4 - IPSec
What's Covered in this Blog
This post covers implementing YubiKey smart card authentication and how it's implemented with a Windows Enterprise CA.
What Is Zero Trust - Recap
Zero Trust is a security framework that assumes no user, device, or network segment is inherently trustworthy, regardless of where it sits in the network. The core principles include:
Verify explicitly - Always authenticate and authorize access.
Use least privilege access – Limit access to only what's needed.
Assume breach – Design as if attackers are already in the network.
How Smart Cards Address Zero Trust Security
Zero Trust is built on the principle of “never trust, always verify.” It requires strict identity verification, least-privilege access, and continuous authentication.
Strong Identity Verification: Smartcards use embedded chips to store cryptographic keys securely. They require something you have (the card) and something you know (a PIN), making them ideal for strong, multi-factor authentication.
Credential Protection: Because authentication happens on the card itself, sensitive credentials are never exposed to the device, reducing the risk of phishing, keylogging, or malware-based theft.
How YubiKey Functions as a SmartCard
YubiKey devices support smart card functionality through their PIV (Personal Identity Verification) capability, which implements the NIST SP 800-73 standard. This allows organizations to use YubiKeys for authentication, signing, and encryption in enterprise environments. The PIV applet on the YubiKey securely stores cryptographic keys and certificates, enabling seamless authentication in Windows Active Directory domains.
Yubikey Core SmartCard Functionality
A YubiKey operates as a hardware security module that:
Stores private keys securely in tamper-resistant hardware
Performs cryptographic operations internally (signing, decryption)
Prevents private key material from ever leaving the device
Key Technical Components
Secure Element: A dedicated cryptographic processor with:
Protected memory for storing private keys and certificates
Hardware-based random number generation
Tamper-resistant design to prevent physical attacks
Certificate Storage Architecture
YubiKeys store certificates in a structured slot system:
24 Total Storage Slots:
Slots 9a, 9c, 9d, and 9e are the primary slots used for certificates
Each slot can store one certificate/key pair
Slot 9a: Authentication (typically used for workstation login)
Slot 9c: Digital Signature
Slot 9d: Key Management (encryption/decryption)
Slot 9e: Card Authentication
YubiKey Smart Card Implementation
To enable smartcard authentication in a Domain, we’ll need to configure Group Policy and create a certificate smart card template.
GPO Settings
Enable the following 3 settings under Computer Configuration > Admin Templates> Windows Components > Smart Card:
Allow certificate with no extended key usage certificate attributes
Allow ECC certificates to be used for logon and authentication
Turn on Smart Card Plug and Play Service
Note: When the Certificates employs Elliptic Curve, the 'Allow ECC certificates to be used for logon and authentication' must be enabled.

YubiKey Smartcards Software
YubiKey functionality requires the following:
Drivers:
Any system where the smartcard is used must have the appropriate drivers installed for the YubiKey to be recognized.
Management Software:
The YubiKey Manager software is needed to configure the devices and set users’ smartcard PINs.
Download:
The software can be downloaded from this link https://www.yubico.com/support/download
YubiKey Manager
To configure a YubiKey open the Manager application
Insert the first YubiKey
Navigate to Interfaces
Deselect all USB types other than PIV

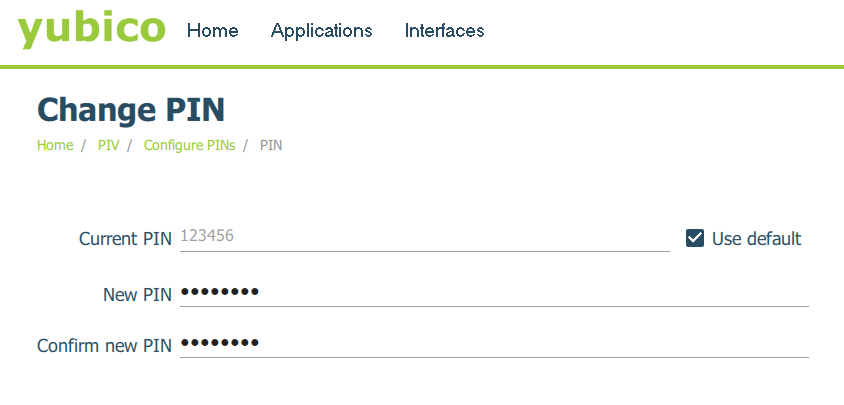
To set the user's PIN, this is the pin used by the user during logon, navigate to:
Applications, select PIV > PIN Management
Configure PIN
Select 'Use Default' or enter 123456
Enter a new PIN
Smartcard Certificate Template
Log in to the Certificate Authority (CA) server using an account with Domain Admin rights or delegated CA Manager permissions.
At the Run prompt, enter certsrv.msc, navigate to Certificate Templates, right-click, and select Manage.
According to YubiKey's guidance, you can use the Smartcard Logon template for deployment, and this is my intention.
However, when the User certificate template is already issued and the Smartcard Logon template is later deployed for enrollment. Testing has shown that overlapping certificate purposes can lead to authentication failures, confusion on the part of which certificate is presented, during smartcard logon.
Duplicate the Smartcard template.
General Tab:
Publish certificate in Active Directory
Do not automatically reenroll if a duplicate certificate exists in Active Directory

Compatibility tab:
Windows Server 2016
Windows 10 / Windows Server 2016

Request Handling tab:
Include symmetric algorithms allowed by this subject
For automatic renewal of smart card certificates, use the existing key if a new key cannot be created.
Prompt the user during enrollment.

Cryptography tab:
Key Storage Provider' and 'ECDH_P384 (ECDH_P512 isn't supported)
Requests must use one of the following providers
Microsoft Smart Card Key Storage Provider
Request hash is 256

The table below compares the equivalent security levels of Rivest–Shamir–Adleman (RSA) and Elliptic Curve Cryptography (ECC). It highlights how ECC achieves the same level of security with significantly shorter key lengths and lower computational overhead. As ECC key sizes grow modestly, the corresponding RSA key sizes increase disproportionately.
RSA | ECC | Devisable by |
512 | 112 | 4.6 |
1024 | 160 | 6.4 |
2048 | 224 | 9.1 |
3072 | 256 | 12.1 |
7680 | 384 | 20 |
15360 | 512 | 30 |
Security tab:
Add Authenticated Users and Autoenroll
A named AD group could be used instead for a more targeted enrollment.

Subject Name tab:
User principal name (UPN) is enabled
E-mail name is unchecked
Add the email address to the User attributes as an alternative to removing.
Enrolment will fail if the E-mail name is enabled and not provided at enrollment.

Smartcard Enrollment
Once the YubiKey drivers are installed on the client machine, the user can enroll for a Smartcard certificate.
Enrollment:
The user opens 'certmgr.msc'
Navigate to Personal > Certificates
Right click on Certificates > All Tasks > Request New Certificate
Select Active Directory
Select the Smartcard template and enroll.

During the enrollment process, when prompted, enter the PIN that was configured earlier during YubiKey setup.

The YubiKey smartcard is now configured for User logon.
Smart Card Misconceptions and Important Next Steps
Windows password authentication is vulnerable to brute force, dictionary, guessing, and phishing attacks. Smartcards significantly reduce these risks. Although commonly thought to eliminate passwords entirely, that's not entirely accurate. When a user account is configured for smartcard authentication within the User AD account, the password is reset one time to a random 120 character string.
Failing to set the "Smart card is required for interactive logon" flag leaves the user's existing password unchanged, allowing them to continue logging in with their original, potentially insecure credentials.
That Password is still there for SSO:
During the AS_REP stage of Kerberos authentication, the Key Distribution Center (KDC) includes the NTLM hash of this password in the PAC to support fallback to SSO when Kerberos is unavailable. The random password is highly resistant to offline cracking, even against well-resourced attacks using tools like John the Ripper. The User password is not so resistant.

Pass the Hash
Enabling smartcard authentication still leaves user accounts exposed to Pass-the-Hash attacks. As previously stated, when the 'Smartcard is required for Interactive logon' is set, the user’s password is reset to a long, random value, but it remains static indefinitely. Without regular password rotation, the account stays vulnerable to Pass-the-Hash. To mitigate this risk, use the script below to refresh user passwords daily.
$scTrue = Get-ADUser -Filter -Properties | where {$_.SmartcardLogonRequired -eq "True"} | Select-Object name,SmartcardLogonRequired
foreach ($user in $scTrue)
{
$name = $user.name
Set-ADUser -Identity $name -SmartcardLogonRequired:$false
Set-ADUser -Identity $name -SmartcardLogonRequired:$true
}Important:
Do not create a scheduled task on a Domain Controller running under a Domain Admin account to flip the smartcard attribute, this is reckless and a serious abuse of privileged credentials.
The correct approach is to:
Create a dedicated service account with delegated 'Write' permissions to the smartcard logon attribute on the Users OU.
Assign the service account 'Log on as a batch job' rights on a hardened member server with the Active Directory tools installed.
Create a scheduled task that runs daily, encoding the PowerShell script in Base64 and embedding it directly in the Task Scheduler's action tab.
That's the Easy Part of the Zero Trust Completed....
The home lab’s in pretty good shape, certs everywhere, and a solid step toward Zero Trust.
But let’s be honest, plastering certificates on every domain object is just providing a false sense of security. There are still gaps, some can be secured, whilst others probably not. Those Linux devices, the pfSense, the wifi AP and the printer all require my attention.
The biggest challenge is monitoring, it's resource hungry and needs an enormous amount of effort to correctly configure. Despite the effort, monitoring will provide a major feature in the Zero Trust architecture, allowing me insight and visibility into the Home Lab.
There's no rest for the wicked and even less for those trying to keep the wicked at bay... thanks and hope content so far is proving insightful.
Next up is IPSec for Linux, after a break and some sleep.
Related Posts:
Part 1 - Zero Trust Introduction
Part 3 - pfSense and 802.1x
Part 4 - IPSec for the Windows Domain


Comments